
Building a Cyber-Resilient Organization
MIke Kell
Recent Posts
Follow me
Building a Cyber-Resilient Organization: Where Strategy Meets Security
Let’s face it—cybersecurity is no longer just a technical responsibility. In today’s digital-first world, it’s a business-critical priority. Every headline about data breaches serves as a stark reminder that resilience isn’t optional—it’s essential.
At Kell Engineering, we’ve seen how aligning cybersecurity with business goals doesn’t just prevent disasters—it builds trust, protects innovation, and drives growth. For example, integrating encryption protocols not only safeguards data but also reassures customers that their information is secure. If you’re curious about practical strategies, check out our Cybersecurity Consulting services.
What Does Cyber-Resilience Really Mean?
Cyber-resilience goes beyond installing firewalls and setting strong passwords. It’s about embedding security into your organization’s culture and processes. For example, consider a business expanding its digital services. If security isn’t baked into the planning phase, it risks customer data breaches or service disruptions.
Here’s a practical tip: Conduct workshops with your executive team and cybersecurity leaders to identify critical business functions and map them to specific security initiatives. For example, prioritizing secure payment processing systems when launching an e-commerce platform could prevent issues down the line.
We’ve worked with organizations to align security with business goals. Learn more about building resilience through our Cybersecurity Consulting services. You can also explore frameworks like NIST’s Cybersecurity Framework for actionable insights.
Why the Boardroom Matters
Cybersecurity leadership starts at the top. Boards of directors must make cybersecurity a priority, not just an IT concern. For instance, by dedicating time in meetings to cybersecurity progress and risks, boards can ensure their organizations stay ahead of threats.
Consider creating a dedicated cybersecurity committee or setting KPIs that measure the impact of security on business outcomes, such as a reduction in data breaches affecting customer trust. Kell Engineering has guided leadership teams in developing these metrics—check out our Cybersecurity Consulting page to see how we can help.
For inspiration, read how major corporations like Target overhauled their board-level cybersecurity strategy after facing high-profile breaches.
Balancing Risk and Reality
Let’s be real: No organization can eliminate risk completely. The key is balancing security, costs, and business continuity. For example, using a layered security approach—combining employee phishing training with intrusion detection systems—provides strong protection without overextending resources.
Consider tools like automated threat detection platforms, which can flag risks in real time. For example, deploying a system that alerts teams to vulnerabilities in critical software prevents risks from escalating. Check out Kell Engineering’s Cybersecurity Consulting services to learn how we implement these strategies.
Want to dive deeper into risk management frameworks? Explore FAIR’s quantitative risk analysis model for translating technical risks into financial terms that leadership teams can easily understand.
Compliance Without the Headache
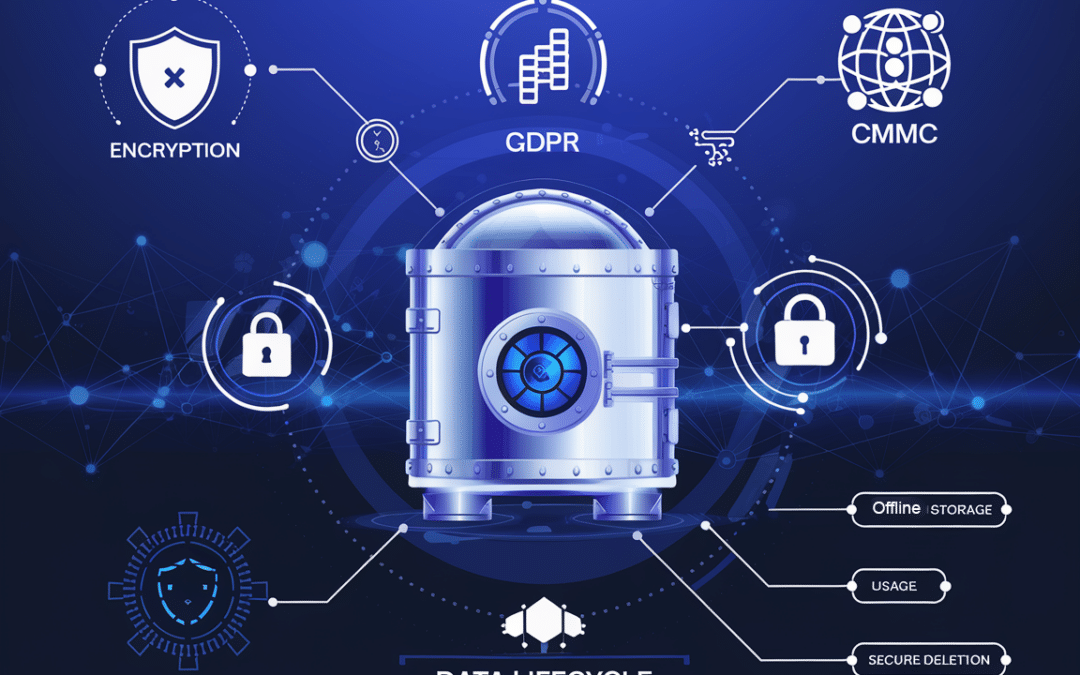
Regulations like GDPR, HIPAA, and CMMC can feel overwhelming, but they’re more than just checklists. Compliance is an opportunity to show customers and stakeholders that you value their trust. For example, adopting GDPR-compliant data privacy policies demonstrates your commitment to safeguarding personal information, which can enhance customer loyalty.
For organizations in the defense industry, compliance with the Cybersecurity Maturity Model Certification (CMMC) is critical. Achieving certification isn’t just about meeting regulatory requirements—it’s about securing your position in the supply chain. Our team has extensive experience helping organizations achieve CMMC compliance. Learn more about our approach on our Cybersecurity Consulting page.
For practical guides on compliance, visit CMMC Accreditation Body or GDPR.eu.
Ready to Build Resilience?
Cyber-resilience isn’t just a buzzword—it’s your competitive edge. It’s about creating a secure foundation for growth, innovation, and trust. At Kell Engineering, we specialize in helping organizations like yours take a proactive approach to cybersecurity.
Whether you’re looking to align cybersecurity with your business strategy, manage risks more effectively, or navigate complex compliance requirements, we’re here to help. Visit our Cybersecurity Consulting page to see how we can support your journey.
Let’s get started—your resilience is your greatest asset.



0 Comments