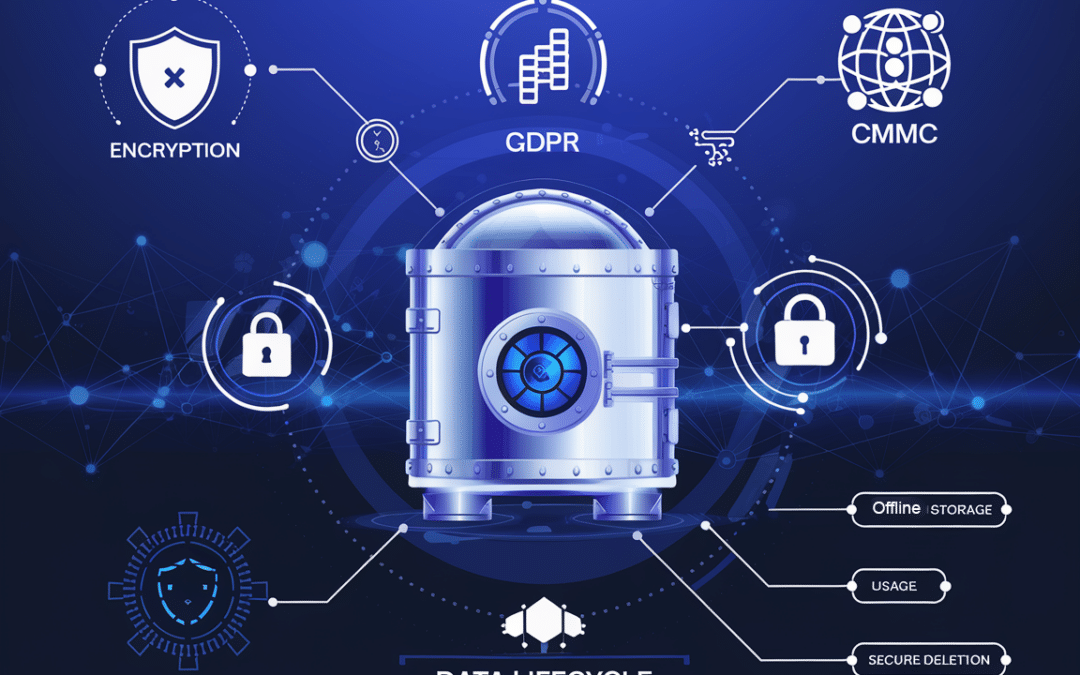
Governance, Risk, and Compliance (GRC) frameworks empower organizations to manage cyber risks effectively, and as a board member, you have a pivotal role in steering these efforts. This guide provides a practical roadmap to help you oversee cybersecurity strategies,...