Kell Engineering

Network and Cyberspace Operations Consulting

Discover a better approach to meet your business’s information needs with Kell Engineering’s Unified Information Technology capabilities. Say goodbye to complexity and regain your sanity as we streamline your technology landscape for optimal efficiency. Our best-of-breed techniques distill the best practices from various business areas, creating a tailored solution for your specific needs. Uncover hidden opportunities, save time, talent, and money, and future-proof your business with Kell Engineering. Strike the perfect balance between capability, growth, and profitability and position your business for sustained success.
Find out about a better approach to your information needs for your business
Unified Network and Cyberspace Technology
Unified Information Technology: Say goodbye to complexity and regain your sanity! Our approach to Unified IT encompasses Networks, Development Operations, and more, streamlining your technology landscape for optimal efficiency.
Balance of Capability, Growth, and Profitability: Discover the sweet spot where your business thrives. Kell Engineering helps you strike the perfect balance between capability, growth, and profitability.
Experience
Over 38 Years of Expertise: With a proven track record of providing cutting-edge Information Technology solutions to both the US Government and commercial enterprises, Kell Engineering brings unparalleled experience to the table.
Business Efficiency
Best-of-Breed Techniques: We distill the best practices from various business areas – financial, operations, marketing, contracts, legal, and IT – to create a tailored solution for your specific needs.
Take the Leap Towards Efficiency:
Uncover Hidden Opportunities: Learn about a better approach to meet your business’s information needs. Our solutions transcend silos, bringing together disparate elements into a cohesive, high-performing whole.
Save Time, Talent, and Money: No more wasted resources! Kell Engineering ensures that your investment in time, talent, and money yields maximum returns by harmonizing the best practices and techniques.

Cybersecurity Governance: A Practical Guide for Board Members
Governance, Risk, and Compliance (GRC) frameworks empower organizations to manage cyber risks effectively, and as a board member, you have a pivotal role in steering these efforts. This guide provides a practical roadmap to help you oversee cybersecurity strategies,...
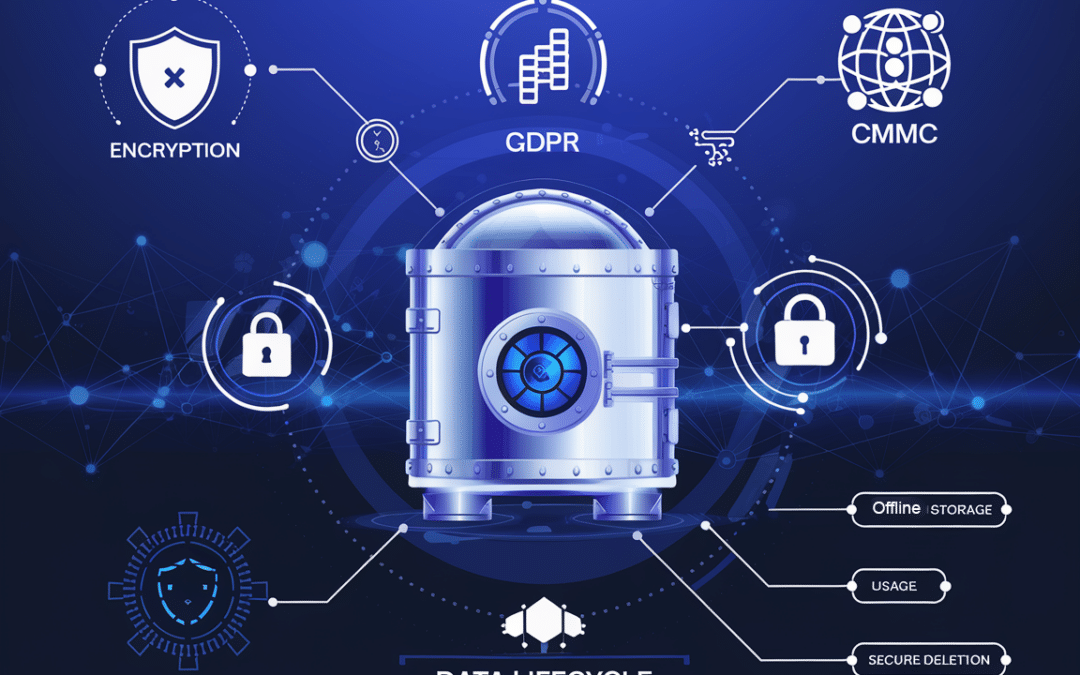
Data Protection and Privacy: A Strategic Priority for Board Members
Let’s talk about why data protection and privacy are critical for the success and resilience of the organizations you oversee. You’ve probably heard the phrase “data is the new oil”—and it’s true. Data drives business decisions, innovation, and competitiveness. But...
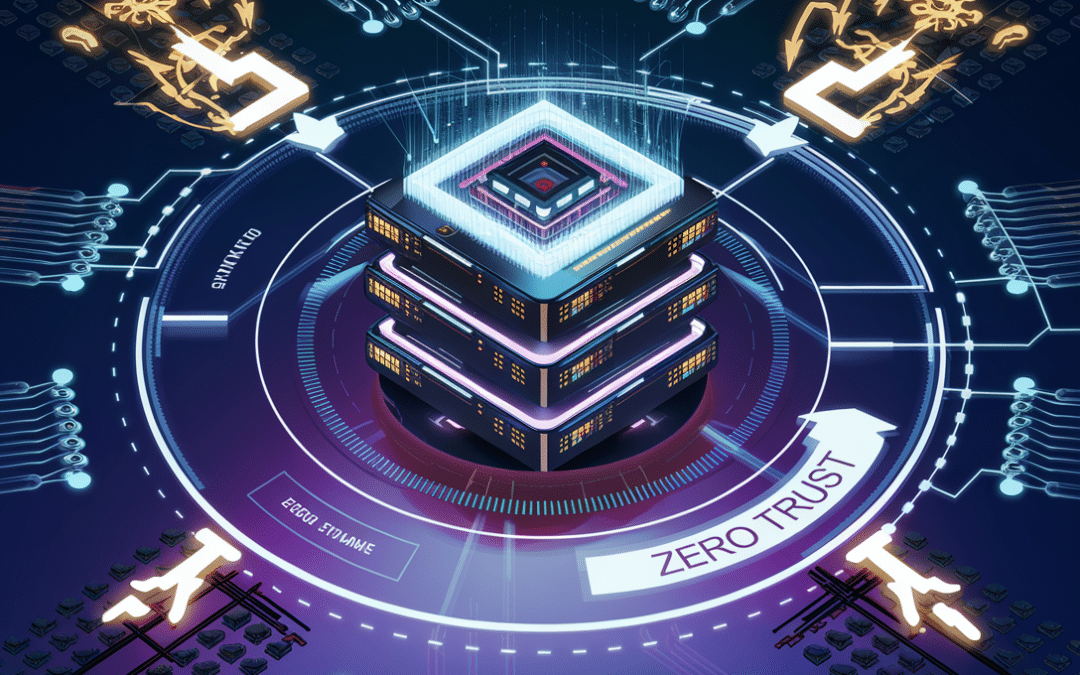
Building a Cybersecurity Fortress: Network Security Fundamentals for Executives
In today’s cyber landscape, a secure network isn’t optional—it’s essential. From firewalls to encryption, and the transformative power of Zero Trust, network security forms the backbone of modern business resilience. Learn how foundational tools, advanced strategies, and proactive vulnerability management can safeguard your organization from evolving threats while enabling operational success.
Building a Cyber-Resilient Organization
Building a Cyber-Resilient Organization: Where Strategy Meets Security Let’s face it—cybersecurity is no longer just a technical responsibility. In today’s digital-first world, it’s a business-critical priority. Every headline about data breaches serves as a stark...
Basic Concepts for Networking and Cybersecurity
In today’s interconnected business world, networking and cybersecurity aren’t just technical concerns—they’re strategic assets. Executives who grasp these fundamentals can make more informed decisions, enabling growth, agility, and resilience. As concepts like Zero Trust and AI gain traction, it’s critical to recognize that they’re rooted in longstanding principles, now enhanced by modern advances. Understanding these basics equips leaders to leverage technology effectively and anticipate future needs in a fast-evolving digital landscape.

Future-Proof Your IT Operations: ITAM, ICAM, and ITSM for CMMC 2.0 Success
In today’s rapidly evolving Defense Industrial Base (DIB) sector, the integration of IT Asset Management (ITAM), Identity, Credential, and Access Management (ICAM), and IT Service Management (ITSM) has become essential for ensuring both cybersecurity resilience and...

Policy Requirements to Pass CMMC 2.0 Assessments
Introduction The Cybersecurity Maturity Model Certification (CMMC) is a critical requirement for DoD contractors, ensuring that sensitive federal contract information (FCI) and controlled unclassified information (CUI) are adequately protected. As the CMMC framework...

The Evolution of U.S. Army Communications: From TRI-TAC to the Unified Network
While the tools and technologies have evolved—from the TRI-TAC systems of the 1980s to the cutting-edge Unified Network of today—the fundamental principles guiding U.S. Army communications have remained the same: ensuring secure, reliable, and seamless connectivity across all levels of operation. This continuity underscores the enduring mission to keep our forces connected, informed, and ready for any challenge.

Mastering CMMC Scoping: A Step-by-Step Guide for DoD Contractors
Ensuring CMMC compliance is crucial for DoD contractors. This comprehensive guide walks you through the steps for scoping CMMC Level 1 self-assessment and Level 2 third-party audits. Learn how to identify and protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) across HR, Finance, Operations, Contracts, and Business Development systems. Follow our detailed instructions to implement essential security controls, prepare for audits, and maintain continuous improvement. Stay compliant, secure your data, and protect your contracts with our expert insights and practical examples.

Mastering Trade-Offs: The Ultimate Guide for IT Network Planning Solutions
In the intricate world of IT network planning solutions, where every decision is akin to a strategic move on a digital chessboard, mastering the art of trade-offs becomes paramount. Welcome to a realm where solution architects and planners navigate the labyrinthine...
Find out about a better approach to your information needs for your business
Find out about a better approach to your information needs for your business
Photos by Dmitri Popov and Billy Huynh on Unsplash
