
Building a Cybersecurity Fortress: Network Security Fundamentals for Executives
MIke Kell
Recent Posts
Follow me
Why Network Security Should Be a Boardroom Topic
Executives must view network security as a strategic priority that underpins trust with clients, investors, and employees. This guide explores how foundational network security practices can be integrated into modern business operations.
Secure Networks: The Heart of Resilient Organizations
Layered security, or “defense in depth,” is a proactive strategy that ensures vulnerabilities in one area are mitigated by strengths in others. Coupled with emerging models like Zero Trust and SASE, this approach reinforces defenses against evolving threats.
Most frameworks today, like the NIST Cyber Security Framework or the CIS Critical Security Controls, recognize the need for layered network defense to prevent the exploitation of single points of failure.
Adapting to remote and hybrid work environments demands vigilance. From Endpoint Detection and Response (EDR) to Mobile Device Management (MDM) tools, prioritizing device and data security is critical. Secure collaboration platforms like Microsoft Teams or Zoom enhance productivity without exposing sensitive information when appropriately configured.
A secure network isn’t just an IT responsibility—it’s your organization’s foundation for resilience. Is your network ready for today’s challenges?
Firewalls: The Gatekeepers
Firewalls are your network’s gatekeepers, analyzing and filtering incoming and outgoing traffic based on pre-established security rules. They are the digital equivalent of security checkpoints, deciding who gets access and who doesn’t. Without firewalls, your network is exposed to unrestricted traffic, increasing the risk of unauthorized access and malicious activity.
A well-configured firewall blocks known threats and helps enforce organizational policies. For instance, blocking access to non-essential websites can reduce the risk of malware infections introduced through phishing campaigns or malicious downloads. Modern firewalls also incorporate advanced features such as deep packet inspection, allowing organizations to inspect the contents of data packets for potentially harmful content.
For organizations transitioning to more advanced security strategies, firewalls remain integral to the multi-layered defense model. Pairing firewalls with other tools, such as intrusion prevention systems, ensures your network maintains a robust initial line of defense. Regularly updating firewall configurations and reviewing logs are essential to ensure they continue protecting against evolving threats.
IDS and IPS: Watching Your Back
While firewalls filter traffic, IDS and IPS ensure nothing slips through. Imagine a guard who spots suspicious behavior and can act on it. IDS monitors traffic for anomalies, while IPS proactively blocks threats before they can be harmed. Together, they provide a one-two punch, alerting you to problems while mitigating risks.
For example, consider a scenario where an attacker attempts to exploit a vulnerability in your network by sending a stream of malicious traffic. IDS c
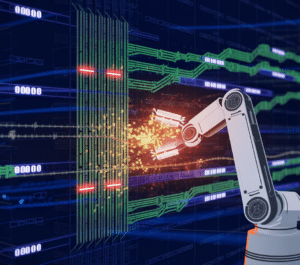
Intrusion detection and prevention: Keeping threats at bay with advanced monitoring
an flag the activity and alert the IT team, while IPS can automatically drop the malicious packets and prevent further attempts. This combination of detection and prevention ensures visibility and action, minimizing the response time to threats.
Deploying IDS/IPS systems is crucial for organizations with sensitive data or high-profile operations. To maximize effectiveness, these systems should be configured to recognize your network’s unique traffic patterns, reducing false positives and ensuring that genuine threats are addressed promptly. Regular updates to treat signatures and behavioral patterns are vital for maintaining effectiveness.
VPNs: Bridging the Gap
Virtual Private Networks (VPNs) are essential for securing remote access in today’s distributed work environments. A VPN creates an encrypted tunnel between a user’s device and the organization’s network, ensuring that data remains private and secure during transmission. This protection is particularly critical when employees connect to the network over public Wi-Fi or other unsecured Internet connections.
For example, consider a traveling employee accessing sensitive corporate data from an airport lounge. Without a VPN, cybercriminals could intercept their connection using man-in-the-middle attacks. By routing their traffic through a VPN, the data is encrypted, making it unreadable to anyone attempting to eavesdrop. This feature is invaluable for individual employees and for safeguarding the entire organization from potential breaches.
Beyond basic encryption, an ideal VPN solution should include several advanced characteristics to maximize its security and usability. First, the VPN must use robust encryption protocols, such as OpenVPN or IKEv2/IPsec, considered industry standards for strong security. Second, it should provide a no-logs policy, ensuring that the VPN provider does not record or store user activity. This is especially important for industries handling sensitive or regulated data, such as healthcare or finance, where privacy is paramount.
Scalability and ease of use are key considerations for deploying VPNs in an enterprise setting. Organizations with large remote workforces require VPN solutions that can handle multiple simultaneous connections without sacrificing performance. Furthermore, user-friendly interfaces and seamless integration with existing systems encourage adoption and minimize employee resistance. For instance, a cloud-based VPN that integrates with single sign-on (SSO) systems can simplify the login process, reducing end-user friction while maintaining security.
Despite their advantages, VPNs are not without limitations. Traditional VPNs can introduce latency, especially when routing traffic through geographically distant servers. Additionally, as businesses increasingly rely on cloud services, VPNs may struggle to provide the granular control required for modern workflows. This is where complementary technologies, such as Secure Access Service Edge (SASE) or Zero Trust Network Access (ZTNA), come into play. These tools extend the principles of VPNs while addressing their shortcomings, offering more flexible and scalable solutions for securing distributed workforces.
In summary, VPNs remain a cornerstone of network security, providing essential protection for remote employees and sensitive data. However, organizations should carefully evaluate their VPN solutions, ensuring they meet the demands of modern work environments while considering emerging technologies to enhance and extend their security posture.
Encryption: Protecting What Matters
Encryption is the last line of defense. Encryption is the backbone of data security, ensuring that sensitive information is protected, whether in transit or at rest. Encryption transforms readable data into an unreadable format that can only be deciphered with the correct decryption key. Even if attackers manage to breach your defenses, encrypted data remains useless without access to the key.
Encryption can safeguard emails, financial transactions, and stored data. For example, a company using AES-256 encryption for its customer database can ensure that the information within remains secure even if the database is stolen. This is especially critical for industries such as healthcare and finance, where data breaches can lead to regulatory penalties and loss of customer trust.
Organizations should adopt end-to-end encryption for communication tools, ensuring that messages are secure throughout their journey. Encryption should also extend to backup systems, where sensitive data is often stored. Regular audits of encryption protocols and ensuring the proper management of encryption keys are critical for maintaining this essential layer of security.
Multi-Factor Authentication (MFA): A Simple but Effective Barrier
Multi-factor authentication (MFA) is a straightforward yet powerful way to prevent unauthorized access to sensitive systems. By requiring at least two forms of verification—such as a password and a code sent to a mobile device—MFA significantly raises the bar for attackers. Even if one factor, like a password, is compromised, the second factor is an additional safeguard.
MFA is particularly effective against phishing attacks. For example, if an employee inadvertently provides their login credentials to a malicious actor, MFA ensures that the attacker cannot access the system without the second verification step. This added layer of protection is invaluable in remote work environments where employees often access company systems from various locations.
To maximize MFA’s benefits, organizations should integrate it across all critical systems, from email and collaboration platforms to cloud-based applications. Educating employees about MFA’s importance and how it works can further enhance its effectiveness, ensuring compliance and minimizing resistance to its implementation.
Addressing Vulnerabilities
Network devices such as routers, switches, firewalls, and access points are critical components of your IT infrastructure. However, they also represent some of any network’s most frequently targeted vulnerabilities. Unpatched firmware, misconfigured settings, and lax access controls can turn these devices into entry points for attackers, compromising the entire network. Understanding and addressing these vulnerabilities is essential to maintaining a secure and resilient network.
One of the most significant vulnerabilities in network devices is outdated firmware or software. Device manufacturers regularly release updates to patch security flaws, but many organizations fail to apply these updates promptly. This creates an opportunity for attackers to exploit known vulnerabilities. For instance, in 2020, attackers leveraged unpatched vulnerabilities in VPN appliances to gain unauthorized access to enterprise networks. A timely update would have prevented the breach.
To address this issue, organizations should implement a robust patch management program. This includes maintaining an inventory of all network devices, subscribing to manufacturer security bulletins, and scheduling regular updates during maintenance windows to minimize downtime. Automating updates where possible can further streamline this process, ensuring vulnerabilities are addressed promptly without relying on manual intervention.
Misconfigured network devices are another common vulnerability. Default settings—such as factory-set usernames and passwords—are particularly problematic. Attackers can exploit these to gain unauthorized access with minimal effort. For example, in 2021, a significant ransomware attack targeted network-attached storage (NAS) devices with default credentials, encrypting critical data for ransom.
Organizations must adopt security best practices to mitigate these risks. This includes changing default credentials immediately upon installation, turning off unnecessary services, and enabling secure configurations such as encrypted communication protocols (e.g., HTTPS, SSH). Configuration baselines should be established, and regular audits should be conducted to ensure all devices adhere to these standards. Configuration management tools can help enforce these policies across large networks, reducing the risk of misconfigurations.
Inadequate access controls on network devices can lead to privilege escalation attacks, where an attacker gains unauthorized administrative privileges. For example, if an attacker compromises a low-level account with broad access to network management interfaces, they could reconfigure devices, intercept traffic, or turn off critical systems.
To prevent such scenarios, organizations should follow the principle of least privilege. This means granting users and devices only the permissions necessary to perform their tasks. For instance, a network technician responsible for monitoring traffic should not be able to modify firewall rules. Role-based access control (RBAC) is an effective strategy for implementing least privilege, allowing administrators to assign permissions based on specific roles and responsibilities. Multi-factor authentication (MFA) should also be enforced for all administrative accounts, adding an extra layer of security.
Addressing vulnerabilities is not a one-time effort but an ongoing process. Regular vulnerability scans can identify issues such as outdated firmware, misconfigurations, and weak access controls. These scans should be complemented by continuously monitoring network devices to detect anomalous behavior. For example, unusual login attempts or configuration changes outside scheduled maintenance windows could indicate a potential compromise. One of the definitive sources of vulnerabilities is the US Government’s Cybersecurity & Infrastructure Security Agency (CISA) Vulnerability Database.
Organizations can use specialized tools such as Security Information and Event Management (SIEM) systems to aggregate and analyze logs from network devices. Integrating these tools with automated response mechanisms ensures that detected threats are quickly mitigated, minimizing potential damage.
Embracing Zero Trust and SASE
The Zero Trust model represents the pinnacle of modern cybersecurity. Unlike traditional models that assume internal traffic is trustworthy, Zero Trust assumes that threats can come from anywhere—inside or outside the network. Every access request, user, and device is verified continuously, ensuring only authorized entities can interact with critical resource

Zero Trust: Verifying every access point for ultimate security
s.
Zero Trust involves several principles, including micro-segmentation, continuous authentication, and the principle of least privilege. For example, a pharmaceutical company implementing Zero Trust may ensure that researchers only access the specific datasets required for their projects, with all access continuously monitored and logged.
Transitioning to a Zero Trust model requires significant planning and investment. It involves integrating tools like Secure Access Service Edge (SASE), which combines security and networking into a unified framework, and Zero Trust Network Access (ZTNA), which verifies every request at the application layer. Organizations embracing Zero Trust often see improved security posture and reduced risk, especially in environments with remote workforces and diverse devices, for an authoritative perspective on Zero Trust principles and implementation.
Forrester Zero Trust Resources.
Building a Resilient Network for the Future
In an era where cyber threats are relentless and ever-evolving, securing your network is more than a technical necessity—it’s a strategic imperative. Addressing vulnerabilities in network devices, deploying robust tools like firewalls and VPNs, and adopting advanced models such as Zero Trust are not just best practices; they are essential components of a resilient cybersecurity strategy. By committing to continuous monitoring, timely updates, and strict access controls, organizations can stay ahead of attackers and protect their critical assets. For executives, the path forward lies in fostering a culture of security that prioritizes vigilance, adaptability, and innovation. A secure network is not just the backbone of IT—it’s the foundation for sustainable growth and trust in a digital-first world.

A secure digital ecosystem with interconnected glowing devices, shields, and locks, surrounded by business professionals reviewing a network plan
This is part of an ongoing series of blogs focused on cybersecurity and network fundamentals for business executives. You can see other articles on the Kell Engineering Blog.




0 Comments